In the digital age, X Chat data privacy and communication security are paramount. Whether it’s personal messaging, business correspondence, or government communication, users expect their digital interactions to remain confidential and protected. However, recent revelations have sparked widespread concern among cybersecurity experts and users alike: X Chat, the social messaging platform integrated into Elon Musk’s X (formerly Twitter), has reportedly failed basic security and encryption tests.
This failure not only undermines user trust but also raises serious questions about how X manages sensitive data. With millions relying on X Chat for personal and professional communication, the implications of such vulnerabilities are profound.
This detailed analysis explores what went wrong, why encryption matters, the findings of recent security audits, how experts have responded, and what users can do to protect their privacy in the wake of these troubling revelations.
Understanding Encryption and Its Importance
Before diving into the X Chat case, it’s essential to understand what encryption is and why it’s the backbone of digital communication security.
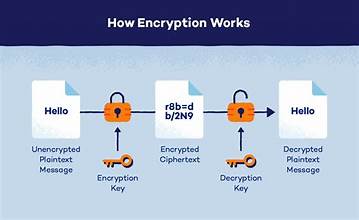
Encryption is the process of converting information into a code to prevent unauthorized access. In messaging apps, this often takes the form of end-to-end encryption (E2EE), where only the sender and recipient can read the messages. Even the service provider cannot decrypt them.
Apps like Signal, WhatsApp, and Telegram (in secret chats) have long promoted their end-to-end encryption systems as a way to protect user privacy from hackers, surveillance agencies, and even the platforms themselves.
When encryption fails—or is implemented improperly—it opens the door to:
- Data breaches
- Unauthorized surveillance
- Message interception
- Identity theft
- Corporate espionage
Given that X Chat was marketed as a secure and private communication tool, the news that its encryption protocols are fundamentally flawed represents a serious breach of user trust.
What Is X Chat?
X Chat is the messaging feature of X, the platform formerly known as Twitter. Following Elon Musk’s rebranding of Twitter into X, the platform expanded beyond social networking to become a so-called “everything app”—combining microblogging, payments, live streaming, and messaging.
X Chat was introduced as part of this transformation. It was designed to rival encrypted messengers like WhatsApp, Telegram, and Signal by providing private, real-time communication between users.
In early promotional material, X’s developers claimed that X Chat would include “enhanced encryption protocols” and “state-of-the-art security features” to ensure privacy and protection from external threats.
However, according to multiple independent cybersecurity reports, these promises appear to have fallen flat.
The Security Audit That Exposed the Flaws
A recent independent security audit, conducted by a consortium of cybersecurity experts and ethical hackers, subjected X Chat’s encryption systems to rigorous tests. The results were alarming.
The auditors discovered multiple fundamental security flaws that could allow malicious actors to intercept, read, or manipulate messages sent through X Chat.
The findings can be grouped into several categories:
1. Incomplete End-to-End Encryption Implementation
X Chat claims to use end-to-end encryption. However, tests revealed that encryption is only partially implemented. Certain metadata—such as sender and receiver identities, timestamps, and message routing details—remains unencrypted, making it possible for third parties to infer communication patterns.
Furthermore, the encryption keys are reportedly stored in a centralized database, meaning X (the company) potentially has access to user messages. This is a major violation of the principles of true E2EE, where only users should possess the keys to decrypt their messages.
2. Weak Cryptographic Algorithms
The audit also found that X Chat relies on outdated encryption algorithms, some of which are vulnerable to modern cryptographic attacks. These algorithms, which may have been adequate a decade ago, are no longer sufficient to protect against today’s advanced hacking techniques.
3. Unverified Identity Protocols
Unlike apps such as Signal, which verify the identity of chat participants through security codes, X Chat reportedly lacks a robust verification mechanism. This opens the door to man-in-the-middle (MITM) attacks, where an attacker could impersonate one of the chat participants.
4. Server-Side Message Handling
Perhaps the most concerning revelation is that X Chat’s encryption appears to rely heavily on server-side processing, meaning messages are encrypted and decrypted on X’s servers rather than solely on the user’s device. This effectively nullifies the privacy benefits of E2EE.
5. Vulnerable to Replay and Session Hijacking
Security researchers also demonstrated that X Chat could be manipulated using replay attacks, allowing an attacker to resend old messages or hijack active chat sessions.
The Implications of These Failures
The implications of X Chat’s failed encryption go far beyond technical flaws—they affect millions of users who may have assumed their private conversations were safe.
1. Privacy Risks
If X or external entities can access unencrypted metadata or message content, it raises the possibility of surveillance, profiling, or even data resale.
2. Political and Journalistic Threats
X is used globally by journalists, activists, and political figures. Without strong encryption, their conversations could be exposed to state-level surveillance or hackers, endangering lives and compromising sensitive sources.
3. Corporate Vulnerabilities
Businesses using X Chat for communications could risk data leaks, allowing competitors or hackers to gain access to confidential information, intellectual property, or strategy documents.
4. Legal and Ethical Backlash
If X falsely claimed to offer end-to-end encryption, the company could face regulatory investigations for misleading advertising and failing to comply with privacy laws like the GDPR or California Consumer Privacy Act (CCPA).
Expert Reactions: “A Security Disaster in the Making”
The cybersecurity community has not held back in its criticism.
Dr. Maya Patel, a cryptography expert from the University of Cambridge, called the situation “a security disaster in the making.” She emphasized that any messaging platform claiming E2EE must undergo independent verification before making such claims public.
Renowned cybersecurity researcher Kevin Beaumont tweeted:
“If your encryption key touches a company server, it’s not end-to-end encryption. Period. X Chat fails the most basic test of secure communication.”
Meanwhile, EFF (Electronic Frontier Foundation) issued a statement urging users to avoid relying on X Chat for sensitive conversations until the company provides transparency about its encryption protocols and fixes the exposed vulnerabilities.
Elon Musk’s Response
As of now, Elon Musk has not issued a detailed technical response regarding the audit findings. However, he briefly addressed the issue on X, stating:
“We take privacy seriously. X Chat will undergo continuous security improvements. Expect updates soon.”
While this statement suggests that fixes are forthcoming, critics argue that the company should have prioritized security verification before rolling out the feature.
Musk’s vision of turning X into a super app—combining communication, banking, and commerce—hinges on users’ trust in its security infrastructure. If that trust falters, it could threaten the viability of his broader plans.
Comparing X Chat to Competitors
Let’s take a closer look at how X Chat’s encryption model stacks up against its main competitors:
| App | Encryption Type | Key Management | Independent Audits | Security Reputation |
|---|---|---|---|---|
| Signal | Full End-to-End | User-only keys | Yes | Industry gold standard |
| Full End-to-End (Signal Protocol) | Device-level | Yes | Strong but owned by Meta | |
| Telegram | Partial (Secret Chats only) | User-only for secret chats | Limited | Good but not default |
| X Chat | Partial / Unverified | Server-stored | None | Weak and untested |
This comparison reveals that X Chat is lagging significantly behind established secure messengers, both in technology and in transparency.
The Broader Issue: Tech Companies and False Security Promises
The X Chat case highlights a broader issue in the tech industry: misleading security claims. Many platforms market themselves as “secure” without undergoing proper third-party audits or implementing recognized encryption standards.
This kind of security theater—where companies promote privacy without delivering it—creates a false sense of safety for users, who may unknowingly expose sensitive information.
True digital security requires:
- Transparent encryption protocols
- Open-source cryptographic frameworks
- Independent security audits
- Strict data minimization policies
Until X adheres to these standards, experts warn users to treat its messaging platform as insecure.
User Reactions and Backlash
The revelation has triggered a wave of backlash from users across the platform. Many expressed frustration that X, a platform once trusted for open discussion, might now be exposing their private messages to potential leaks.
Some users even began migrating back to Signal or Telegram, emphasizing that privacy should never be compromised for convenience.
Trending hashtags such as #XChatSecurity and #EncryptionFail emerged as users demanded transparency and accountability from the company.
Steps X Must Take to Regain Trust
To restore credibility, X must take immediate and transparent action. Experts recommend several urgent steps:
- Implement True End-to-End Encryption: Messages should be encrypted and decrypted only on user devices.
- Eliminate Centralized Key Storage: Users must control their own encryption keys.
- Conduct Independent Security Audits: Invite third-party cryptographers to verify claims.
- Open Source the Encryption Protocol: Allow experts to inspect the system for vulnerabilities.
- Enhance User Verification Features: Introduce cryptographic safety numbers or QR verification, like Signal.
- Disclose Data Handling Policies: Clarify how metadata is stored and who can access it.
Failure to implement these steps could permanently damage X’s reputation as a secure communications platform.
What Users Can Do to Protect Themselves
While X works (hopefully) to fix its encryption issues, users can take proactive measures to safeguard their privacy:
- Avoid sharing sensitive information via X Chat.
- Use proven encrypted apps like Signal for confidential discussions.
- Regularly update your software to patch known vulnerabilities.
- Enable two-factor authentication (2FA) on your X account.
- Be cautious of phishing attempts exploiting the security news.
These steps can minimize personal risk until X demonstrates that it can provide genuine encryption.
The Future of X Chat: Uncertain but Salvageable
Despite the controversy, experts believe X Chat’s problems are fixable—if the company commits to transparency and technical rigor.
Elon Musk’s vision of transforming X into an “everything app” could still succeed, but only if privacy becomes a non-negotiable foundation of its design. Security cannot be treated as an afterthought or marketing gimmick—it must be the core architecture.
If X successfully revamps its encryption infrastructure, it could regain user trust. But if it fails, users may permanently abandon the platform in favor of more reliable alternatives.
Conclusion: A Cautionary Tale of Overpromise and Underdelivery
The revelation that X Chat encryption protocols fail fundamental security tests serves as a wake-up call for both tech companies and users.
In a world where digital communication is inseparable from everyday life, privacy cannot be optional. Claims of “secure messaging” must be backed by verifiable, independent, and transparent proof—not just corporate promises.
As users, we must remain vigilant, demand accountability, and prioritize platforms that respect our right to privacy.
For X, the path forward is clear: rebuild trust through action, not words. The company’s response in the coming months will determine whether it remains a key player in digital communication—or becomes a cautionary example of how failing the basics of security can undo even the most ambitious visions.



